The Trust Crisis Driving the Need for Digital Provenance
The digital world will see an explosive growth to 175 zettabytes of global data by 2025. This massive growth in digital content volume brings serious concerns around content authenticity and verification. Recent studies show that 62% of online content could be fake, and companies report 20% more video deepfake cases, highlighting a growing digital trust crisis.
The price tag for ignoring content authenticity is steep. Companies shell out millions of dollars per incident to deal with digital authenticity breaches, misinformation, and synthetic media fraud. This explains why deep-fake detection, AI-generated content verification, and synthetic content verification now play key roles in digital trust frameworks. Gartner has placed digital provenance among the top 10 tech trends that will change IT through 2030. On top of that, the Digital Authenticity and Provenance Act 2025 require organizations to be transparent about their digital content verification and content provenance practices.
This piece gets into why digital provenance matters in 2026 as a foundation for verifiable digital content. We’ll look at how it aids AI content authenticity and the practical ways to implement reliable digital content verification systems as synthetic media and AI-generated content continues to evolve.
The Rise of Synthetic Media and the Need for Content Authentication
Synthetic media has grown from a curious novelty to become commonplace in the modern digital ecosystem. This new wave of AI-created content, including synthetic images, audio, and video, poses unique challenges for content verification and digital trust, unlike traditional user-generated materials.
AI-Generated Content and Deepfake Proliferation in 2026
Synthetic media includes audio, images, and videos created by generative artificial intelligence systems. These digital forgeries, known as “deepfakes,” can now convincingly copy someone’s voice or appearance using advanced AI models. Technology has evolved from basic experiments to sophisticated generative AI tools that produce content that are nearly impossible to distinguish from human-created work.
Numbers tell a compelling story of this change. Detected deepfake cases surged from 500,000 to 8 million between 2023 and 2025, a dramatic 900% increase in synthetic media incidents. Experts predict AI-generated synthetic content could make up 90% of online content by 2026, fundamentally reshaping digital trust and content authenticity
Several key factors drive this growth:
- Easy access to generative AI tools and platforms
- Lower technical barriers to creating convincing AI-generated fakes
- Money-making opportunities that push synthetic media innovation
The generative AI market shows this rapid expansion. Projections show 560% growth between 2025-2031, reaching USD 442 billion. Fraud experts report alarming statistics: 46% have seen synthetic identity fraud, 37% encountered voice deepfakes, and 29% dealt with video deepfakes, underscoring the need for robust digital provenance systems.
Research reveals a more troubling fact. People cannot reliably spot AI-generated voices and often mistake them for real human speech. This problem now affects digital interactions every day, not just technical environments.
Impact of Synthetic Content on Digital Trust and Security
The World Economic Forum lists synthetic media and AI-driven misinformation among the world’s biggest risks. They point to the growing difficulty in telling AI-generated content from human-made material. Business leaders share this worry, 87% see AI-related vulnerabilities as the fastest-growing cybersecurity and digital trust threat through 2025.
Criminals now use AI to create automated phishing attacks. They craft fake emails that look like they’re from friends and make convincing AI-generated voicemails and deepfake videos. Modern voice-cloning AI needs just seconds of audio to copy someone’s voice, letting scammers create fake emergency calls from loved ones.
Money losses paint a grim picture. A company lost USD 25 million in January 2024 when fraudsters used deep-fake technology to pose as their CFO during a video call. Deloitte predicts U.S. fraud losses will jump from USD 12.3 billion in 2023 to USD 40 billion by 2027, growing 32% yearly due to AI-enabled fraud.
The damage goes beyond money. Trust in digital information continues to erode. About 74% of consumers doubt photos or videos, even from trusted news outlets. Election concerns run high, with 94% worried about misinformation’s effect on democratic processes.
People often believe in deep-fake videos’ messages even when warned they’re fake, according to behavioral and psychological studies. We’re approaching what experts call the synthetic reality threshold, where humans need technology to tell real content from fake.
This widespread loss of trust means we need reliable digital provenance systems to verify content. These tools must track digital content’s origin, modification history, and chain of custody throughout its lifecycle.
Digital Provenance & Content Authentication
Understanding Digital Provenance in the Context of AI Content Authenticity
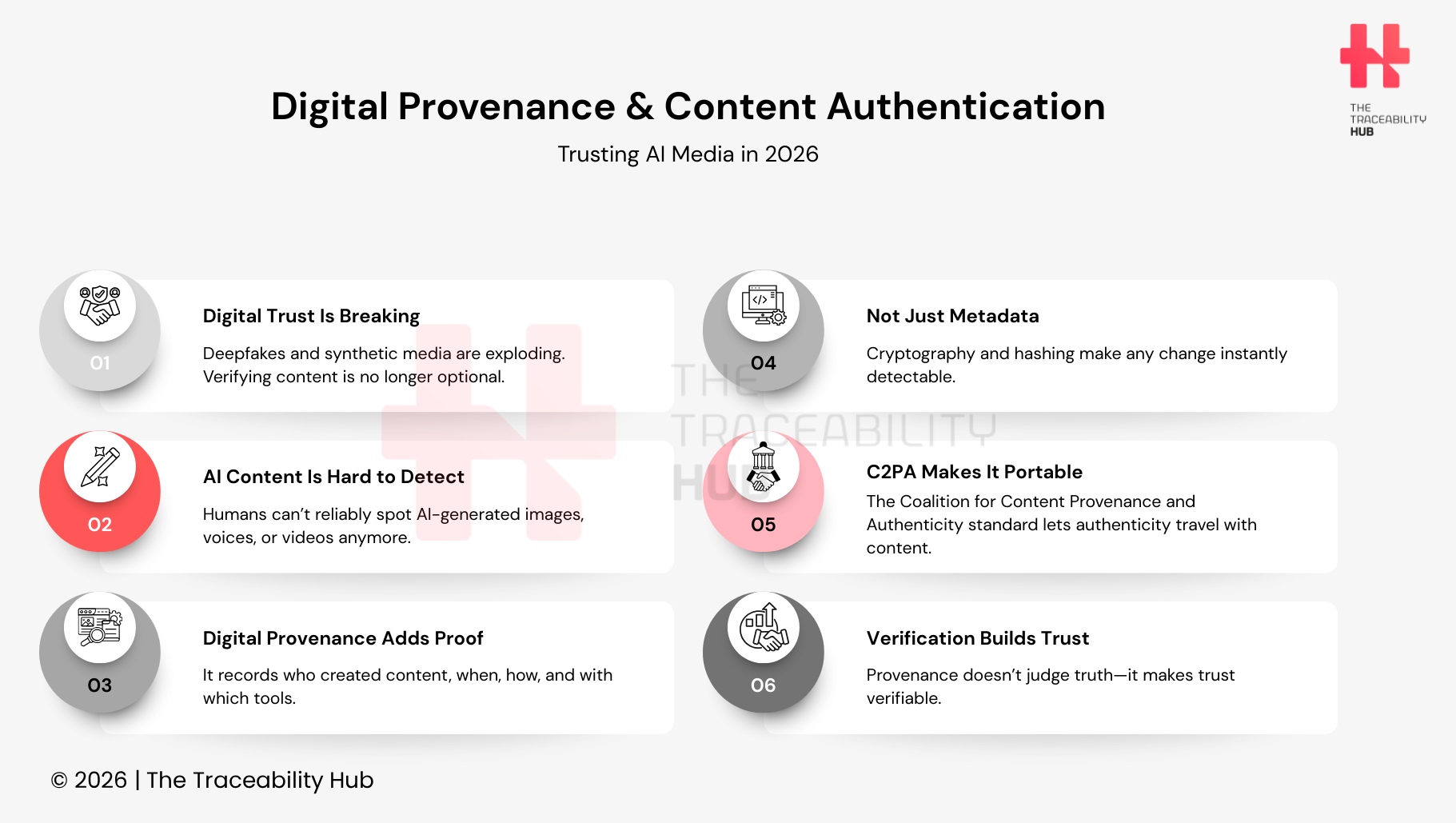
The concept of digital provenance has become a vital framework that establishes trust in the digital world. Gartner lists digital provenance among the top 10 technological trends that will shape IT and cybersecurity through 2030.
Definition and Scope of Digital Provenance
Digital provenance creates a sophisticated system that traces the origin, ownership, and complete history of any digital asset throughout its lifecycle. The art world first used the term “provenance” to document an artwork’s origin, ownership, and changes over time. The digital version creates a detailed content history footprint that follows content, whatever the platforms, formats, or modifications.
Digital provenance answers three basic questions:
- Who created the content? (verified creator identity, devices, software, AI models)
- When and where was it created? (temporal and spatial data)
- Has anyone altered or tampered with the content? (content integrity and authenticity verification)
This detailed tracking works like a “digital identity card” for content that updates as it moves through digital ecosystems and content supply chains. Digital provenance goes beyond simple attribution and establishes a verifiable chain of custody for digital assets from creation to current state.
How Provenance Is Different from Traditional Metadata
Traditional metadata offers simple descriptive information about digital files, such as title, author, format, and size. Digital provenance represents a major step forward from these limited data points.
The key differences include:
- Provenance systems use cryptographic seals with digital signatures and hashing. No one can alter the origin or history of data without detection. The smallest modification to a file creates a completely different hash value that makes changes instantly detectable.
- Provenance updates dynamically, it records every modification, access, or sharing event right away to create a living history of the content. Static metadata needs manual updates, which makes it less reliable.
- Provenance information works across multiple platforms and systems through standardized protocols like C2PA (Coalition for Content Provenance and Authenticity). The provenance data stays intact as content moves between applications, services, and users.
- Stakeholders can verify provenance independently without intermediaries. This verification feature makes digital provenance systems more reliable than traditional metadata.
Role of Provenance in Verifying AI-Generated Content
AI-generated content becomes harder to distinguish from human-created work each day. Digital provenance acts as a critical content verification mechanism. For AI-generated media, provenance data typically has:
- The text prompt used as input for the model
- Name and specifications of the generative AI model
- Creation timestamp
- Identity of the person/entity generating the content
- Later modifications or transformations
The Coalition for Content Provenance and Authenticity (C2PA) developed an open technical standard called “Content Credentials” that works like a “nutrition label” for digital content. This standard lets creators attach verifiable attribution of information and usage signals to their assets.
Digital provenance doesn’t judge content as “real” or “fake.” When an AI tool supports Content Credentials, provenance simply shows that AI generated an image. Users can then make their own informed decisions about the content they see.
Properly implemented provenance systems use cryptographic security methods and tamper-evident design. These systems can detect improper changes or modifications made after applying credentials. This feature helps establish trust in an increasingly synthetic digital world.
Core Components of a Digital Provenance System
Digital provenance systems depend on several interconnected components that work together to build digital trust and verify digital content’s authenticity at scale. These technical elements are the foundations for reliable content authentication frameworks in a digital world filled with synthetic media, AI-generated content, and deepfakes.
Creation Metadata: Author, Timestamp, Device
Creation metadata acts as the starting point for any digital provenance record and documents the essential “who, what, when” details of content origin and authenticity. The creator’s identification, precise timestamp information, device specifications, and geographical location data make up this metadata.
The system captures these critical details automatically when digital content is created to build a foundation for traceability, provenance tracking, and content verification. This metadata helps distinguish between human-created and AI-generated content because provenance data can show specific information about generative models, tools, and prompts used to create synthetic media.
Modification Tracking and Version History
Digital provenance systems keep complete records of every transformation a digital asset undergoes throughout its lifecycle. Timestamps and actor identification documents for each edit, change, or modification to create a transparent audit trail for content authentication.
The chronological version of history reveals how content evolved and makes unauthorized alterations easy to detect. Organizations with substantial content libraries use this modification tracking and version control to see their digital assets’ complete lifecycle as they move across channels and distribution systems.
Ownership and Access Control Records
Ownership records show who currently holds rights to a digital asset, and what permissions exist to be used to modify or distribute it. These records are a core element of digital provenance and content governance, enabling organizations to enforce content integrity and authenticity controls.
Access control implementation guidelines let systems record information about feature creators and limit access to unauthorized users. This component works with digital rights management (DRM) systems to stop unauthorized access and distribution while keeping a complete ownership history trail. The service needs information about who creates features and tries to access them for ownership-based access control to work.
Embedded Cryptographic Signatures
Embedded cryptographic signatures act as the security backbone of modern digital provenance systems. Public Key Infrastructure (PKI) links each change to a specific actor and binds individuals and devices to content through encryption.
The system generates a unique hash value of the digital asset, a “digital fingerprint” even though the smallest modification produces a completely different hash, making tampering immediately detectable. This makes tampering easy to detect and protects the provenance record’s integrity. Security standards require these signatures to use trusted cryptographic methods to secure integrity.
C2PA Standard for Cross-Platform Interoperability
The Coalition for Content Provenance and Authenticity (C2PA) created an open technical specification to document and certify media content’s source and history. This industry standard helps digital provenance data persist across platforms, applications, and formats.
C2PA organizes cryptographically signed records that capture information about item changes, including author, modification, timestamp, and location data. The standard implementation as “Content Credentials” works as a nutrition label for digital content and lets creators attach verifiable authenticity information directly to their work that viewers can access across supported platforms.
How Digital Provenance Enables Trust and Verification
Digital assets need robust verification mechanisms to confirm content authenticity and integrity. Four critical verification pillars create trustworthy digital environments that work together.
Authenticity Validation Using Digital Signatures
Digital signatures act as mathematical and cryptographic algorithms that confirm the authenticity and integrity of digital messages, media, or documents. These signatures create unique “fingerprints” through cryptographic processes to identify specific creators, organizations, or entities.
The verification follows a precise sequence. The sender creates a unique hash of their message and encrypts it with their private key. Both the message and signature go to the recipient. Recipients decrypt the signature with the sender’s public key and compare the resulting hash with one they generate from the received message. Matching hashes show the sender’s identity and prove no alterations happened during transmission, providing strong content authentication and provenance validation.
Integrity Checks through Content Hashing
Content hashing generates identification of fingerprints of digital assets that change if alterations occur at the pixel or byte level. This technique works because hash functions cannot be reversed. A small modification creates an entirely different hash value, which makes changes easy to spot.
To name just one example, a system can allow browsers to confirm that fetched resources arrive without unexpected manipulation by comparing cryptographic hashes. Browsers compare the content against expected hash values in integrity attributes before running scripts or applying style sheets. This approach is foundational to digital provenance integrity checks, AI content verification, and secure content delivery.
Accountability via Transparent Audit Trails
Audit trails create detailed chronological records of every interaction with digital assets, including access, modification, and distribution of events. These permanent records show who accessed what data and from where, creating digital footprints of system interactions. Users know their actions leave permanent documentation, which discourages unauthorized activities.
Organizations use audit trails to detect fraud, break security breaches, and show regulatory compliance. Complete audit trails give necessary documentation to prove regulation of adherence during investigations, which reduces potential penalties and reputation damage.
Real-Time Digital Content Verification Workflows
Modern verification systems merge with existing content workflows to enable immediate authentication without disrupting user experience, for example by delivering forensics-ground detection within seconds, including threat intelligence and context to speed up investigation and response.
Teams can configure these workflows for automated or on-demand verification. Meeting hosts receive custom prompts and optional auto-ejection of detected deepfakes. The C2PA standards help verification systems run on multiple platforms, which ensures interoperability throughout the digital content ecosystem.
Challenges in Implementing Digital Provenance at Scale
Organizations face substantial hurdles while scaling verification systems to implement digital provenance and content authentication systems. Building effective content authentication frameworks requires careful thought.
Balancing Transparency with Data Privacy
Digital provenance systems must strike a delicate balance between transparency, data privacy, and confidentiality. Detailed tracking provides valuable content authentication but creates privacy vulnerabilities. Sensitive personally identifiable information needs protection even within an asset, so not all digital asset information should be available to the public.
Standard provenance implementations often expose private details like organization names, repositories, usernames, emails, and file names to the public. This creates a fundamental dilemma – organizations need to maximize transparency for verification while maintaining proper privacy safeguards.
Scalability Issues in High-Volume Content Environments
The massive volume of digital content puts immense strain on provenance systems. Provenance data can grow several times larger than the original content in Big Data workflows. Rising transaction volumes lead to network congestion and slower confirmation times. Data management becomes more complex as storage capabilities get overwhelmed, affecting compliance and regulation.
Even well-resourced provenance implementations hit throughput limits. Many systems can process only a limited number of transactions per second, which creates bottlenecks during peak usage. Scalability remains a core challenge for enterprise-grade digital provenance systems.
User Adoption and Workflow Integration Barriers
Resistance to change creates obstacles to provenance implementation. Digital provenance systems have learning curves that create adoption barriers, especially when you have less technically proficient users. Even excellent technologies fail without proper management because people aren’t ready to welcome them.
Teams need to modify processes across thousands of content pipelines to understand content authentication, provenance verification, and AI content labeling, to properly implement verification. Many teams lack the digital knowledge to use new tools efficiently, which leads to errors and poor ROI.
Security Risks: Tampering and System Compromise
Provenance system security represents a critical vulnerability. Organizations must ensure their provenance of information stays secure and reliable. Security becomes harder to maintain as networks grow larger, making systems more vulnerable to attacks. Organizations using external provenance services face availability risks. Enterprises might be unable to deploy code during service outages, creating single points of failure in production pipelines.
Many current threat models underestimate emerging risks, leaving digital provenance infrastructures vulnerable to sophisticated attacks.
Digital Provenance as the Foundation of Verifiable Truth
Digital provenance pioneers our defense against misinformation while synthetic media and AI-generated content blur the line between real and artificial content. The massive growth of global data and the alarming rise in deepfake incidents demand resilient content authentication frameworks. On top of that, standards like C2PA show promise to verify content across platforms while protecting content integrity.
Several technical elements form the foundations of digital provenance. Creation of metadata, modification tracking, ownership records, and cryptographic signatures create verifiable chains of custody for digital assets. These systems help organizations confirm content authenticity through digital signatures. They verify integrity through content hashing and track accountability through audit trails with immediate verification processes.
Many challenges still exist. Organizations need to balance transparency with digital privacy concerns. User adoption barriers and security vulnerabilities need thoughtful implementation strategies. The balance between complete tracking and confidentiality remains maybe even the most delicate aspect of provenance systems.
A perfect solution doesn’t exist yet. Digital provenance gives us essential tools to navigate an increasingly synthetic digital world. Authentication mechanisms will become basic infrastructure rather than optional safeguards as AI-generated content becomes identical to human-created work. Organizations that invest in resilient provenance systems today will build digital trust tomorrow. Online credibility’s future depends not just on detecting falsity but on establishing verifiable truths through complete provenance frameworks throughout the entire content’s lifecycle.
Coming soon: CBAM Readiness Checklist: Data, Systems, Suppliers






